Notification about the vulnerability in Xerox FreeFlow Core
September 17, 2025
Dear customers,
We would like to thank you for your continued support towards FUJIFILM Business Innovation products.
Vulnerabilities (CVE-2025-8355~8356)*1 have been found in Xerox FreeFlow Core, which is included in the Xerox FreeFlow Digital Workflow Collection.
- *1 Vulnerability information published by the National Institute of Standards and Technology (NIST)
We apologize for any inconvenience this may cause, but please check if your Xerox FreeFlow Core is compatible with the target version, and if so, take the following actions.
At the time of posting this notice, we have not confirmed any attacks that exploit this vulnerability.
Vulnerability Details
We have found the following vulnerabilities in our product Xerox FreeFlow Core that lead to multiple remote code execution.
- CVE-2025-8355 (High): XXE leading to SSRF (CWE-611)
- CVE-2025-8356 (Critical): Path Traversal leading to RCE (CWE-22, CWE-94)
Eligible Products and Versions
Xerox FreeFlow Core 7.0.0~7.0.11
- How to check the version
- After logging in, click the “?” mark in the upper right corner of the screen and select the “FreeFlow Core Information” menu.
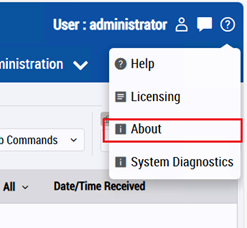
- Check the version on the screen that appears.
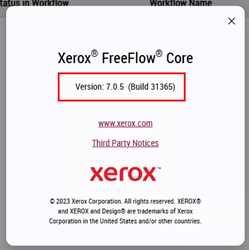
- After logging in, click the “?” mark in the upper right corner of the screen and select the “FreeFlow Core Information” menu.
Correspondence
The vulnerability disclosed this time is potentially present in the Xerox FreeFlow Core, which we provide and support as a product, but we do not provide this functionality as a product feature and do not disclose information about such functionality.
Therefore, vulnerabilities can be avoided as long as you operate within the scope of our functions in an environment protected by a properly configured firewall and follow the following "workarounds".
As a permanent measure, Xerox, which provides FreeFrow Core, provides a separate version of the software to prevent vulnerabilities.
Once we confirm the quality and are ready to provide it, we will provide the information later.
Workaround
As described above, there is no risk of this vulnerability if a properly configured firewall is protected from unauthorized external access.
In addition, the following measures can be implemented to reduce the risk of vulnerabilities without dependence on the network environment in which Xerox FreeFlow Core is used.
- Do not allow connection to a specific port (4004)*2
- *2 The following is how to check the status of a specific port (4004) and how to stop if connection is allowed.
Regarding Checking and Disabling Port 4004 Status
Related Information
Xerox Security Bulletin XRX25-013 for FreeFlow Core
Contact Information
- Customers who have a software support contract
Please contact the Fujifilm Business Innovation subsidiary/distributor where you purchased your software. - Customers who do not have a software support contract
Please contact the distributor where you purchased your software.